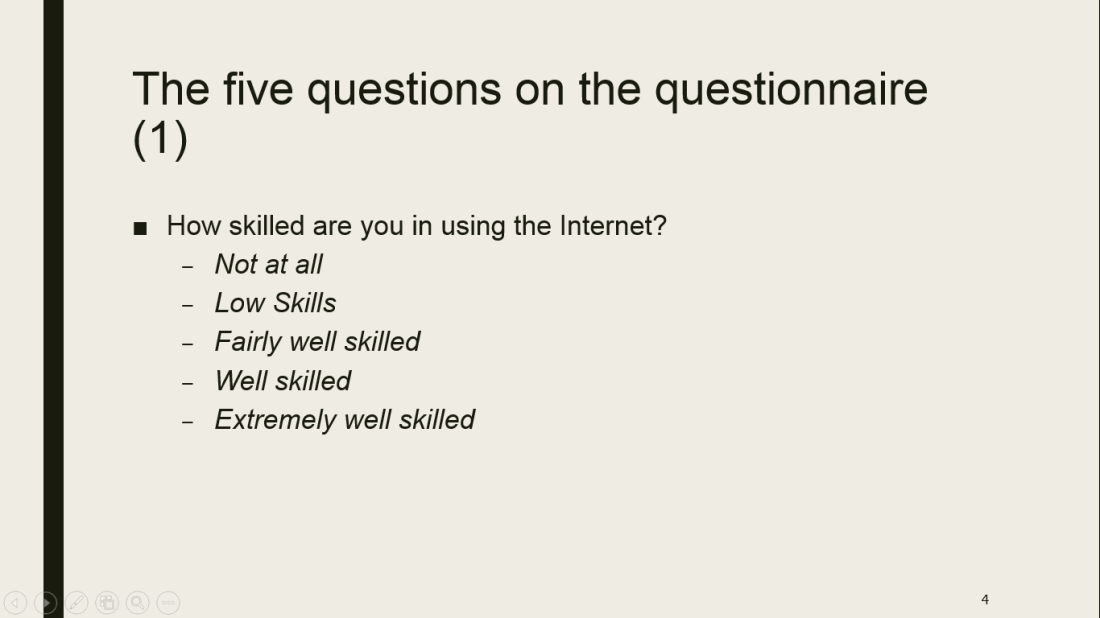
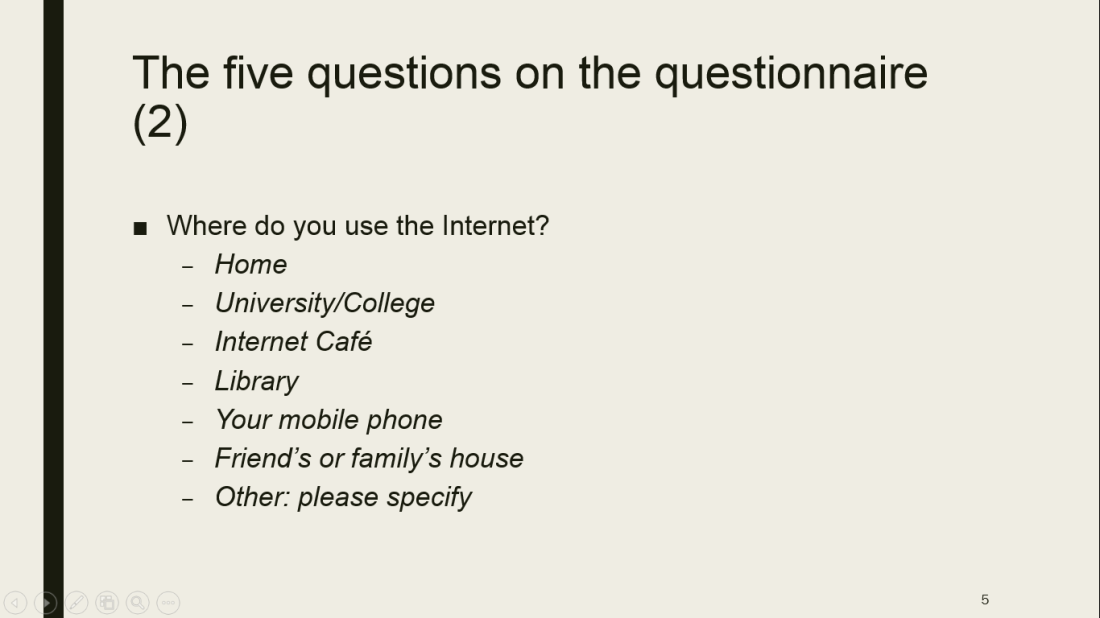
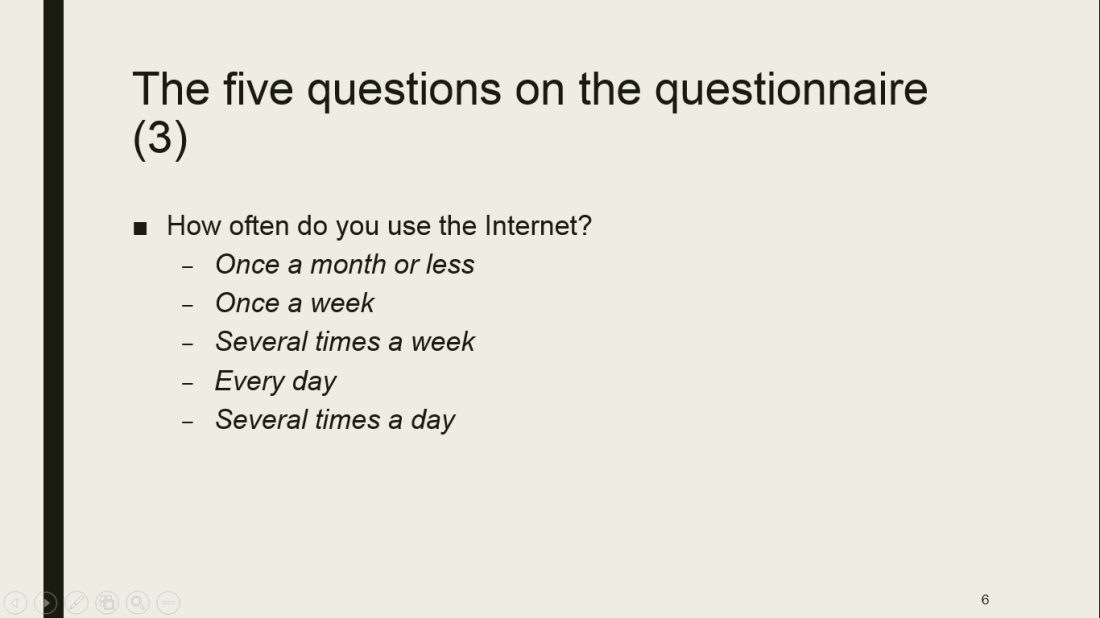
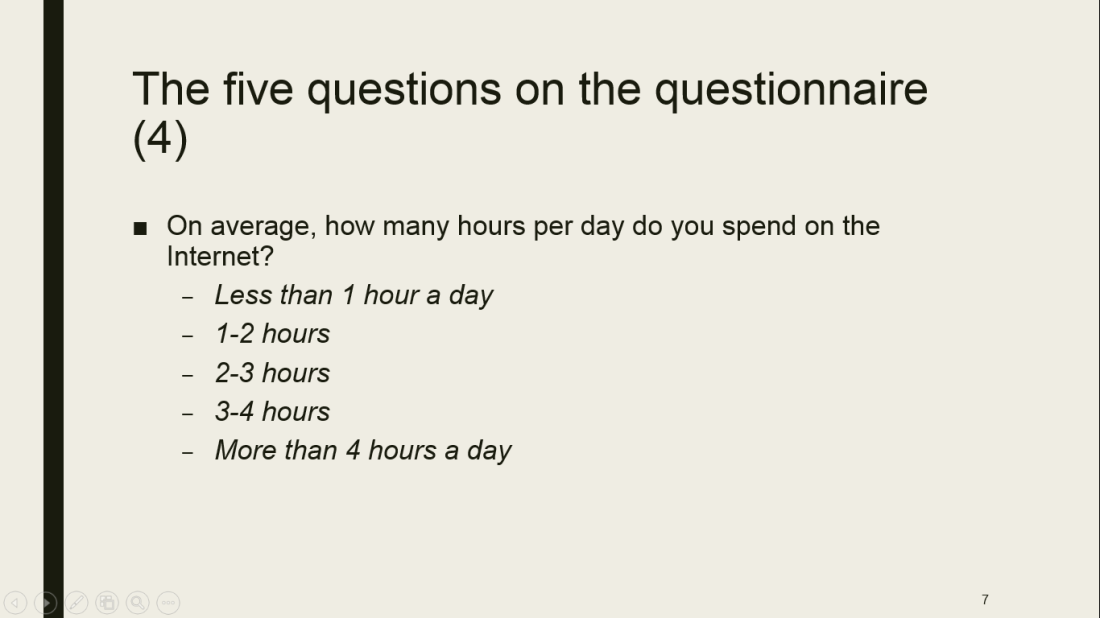
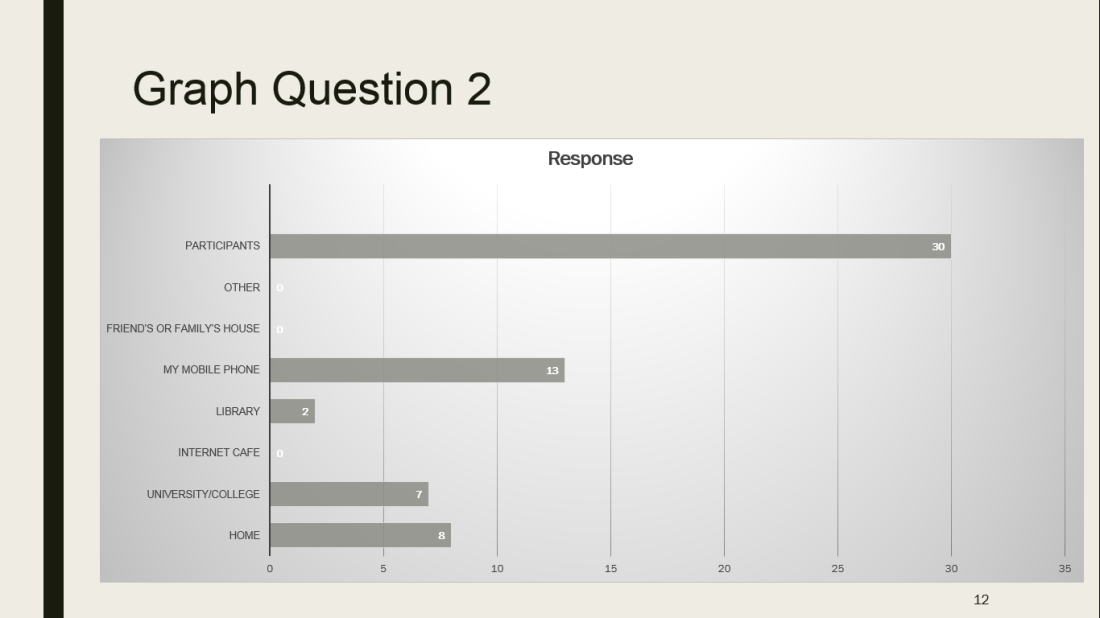
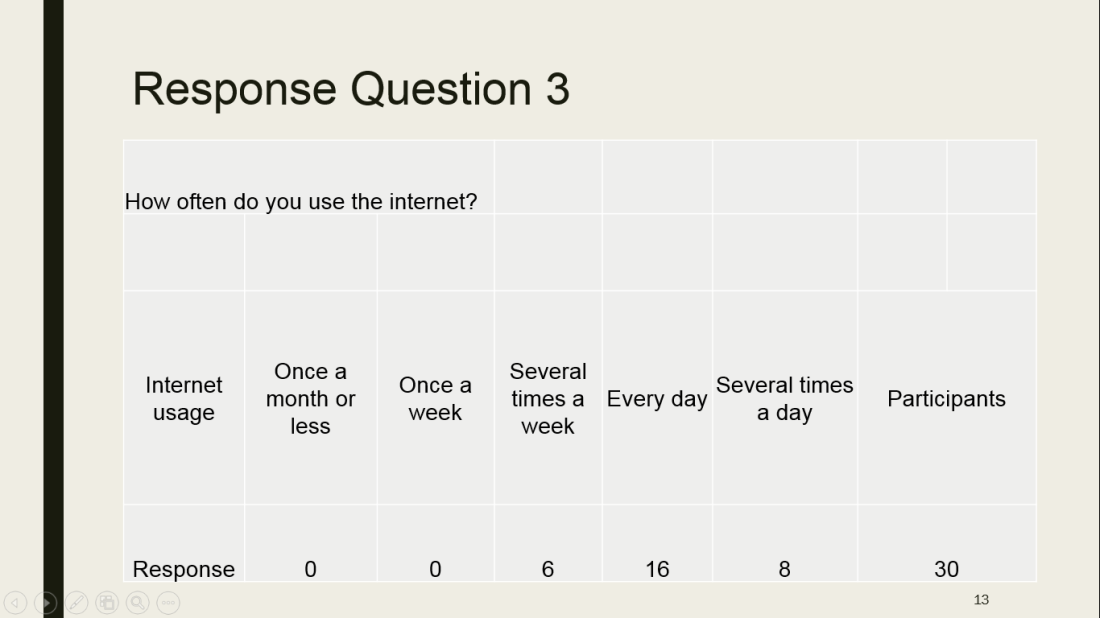
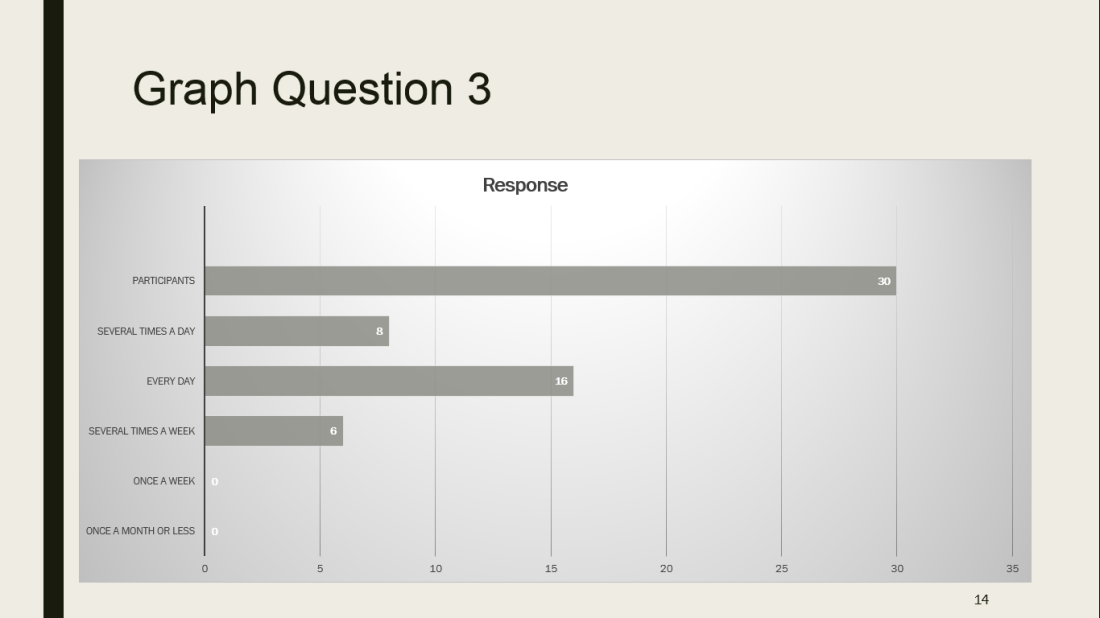
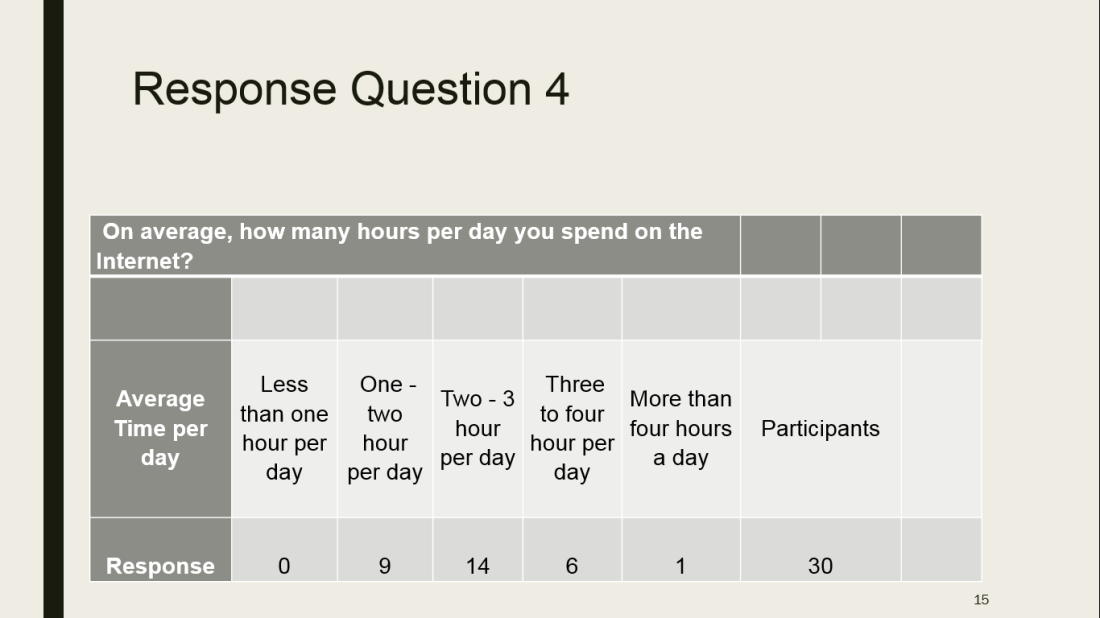
Roberts Blog (2016) quotes the definition of Ribble & Baily of 2007 on digital etiquette as follows:”…the standards of conduct expected by other digital technology users”. Digital etiquette implies how people must act when using the internet. They must behave in an appropriate and accountable manner when using the internet/technology.
The Metropolitan Police of the United Kingdom (n.d.) issued warnings on the dangers associated with inappropriate internet use. The following types of inappropriate behavior of internet use and the possible effects are:
- Privacy
Due to the fact that the internet offers users a lot of freedom, people can act inappropriately, in ways they would not usually do in public. They might post things they would never do when facing people in public, or they might make private information about themselves known. A typical example can be when the person sends a message on his/her future movements going on holiday. If the information gets into the wrong hands, he/she might be burglarized while on holiday. Story Board (2017).
Story Board (2017).
- Cyber bullying
Cyber bullying can be similar to bullying someone on the playground. The target will feel afraid and alone, while the bully will try not to be caught. Cyberbullying can cause psychological, emotional and physical stress which can lead to suicide, impacting negatively on society (Roberts Blog, 2016).Comments, images and videos about a person can be posted online which will upset the victim.
- Cyber bullies can hack into a victim’s personal accounts and harass them.
Due to the fact that they cannot be seen, cyber bullies think they are untraceable, which is incorrect as there are traces of evidence that it has happened.  Story Board (2017)
Story Board (2017)
- Cyber stalking
People are harassed on the internet, which can be as terrifying as forms of stalking. The UK Metropolitan Police (n.d.), states that it is usually women and girls who are the victims. They might for instance be harassed by an ex-lover who is still upset about their break-up. Sexual harassment impacts negatively on society as people are can be traumatized for the rest of their life (Roberts Blog, 2016).
 Story Board (2017).
Story Board (2017).
- Identity Theft
The more information you make available of yourself on the internet, the greater the risk of identity theft. It might be very tempting to react to a special offer or competition making your personal details such as phone number, address, banking information or identity number known. The chances of fraud or theft while misusing your identity number is a possibility.
 Story Board (2017).
Story Board (2017).
- Sexting
According to the UK Metro Police (n.d.) sexting refers to:” sending and receiving rude messages or videos of:
- naked pictures
- ‘underwear shots’
- any sexual texts, images or videos”
The images or videos can be sent from somebody you have met on the internet. Sexting can happen because:
- You conform to peer pressure, for example sending explicit to friends.
- You are harassed, threatened or blackmailed into sending pictures.
- someone keeps asking for things and you feel that it’s easier just to ‘give in’
- You think you ‘owe’ your boyfriend or girlfriend or you think you can trust them because you love them.
- You feel proud of your body and want to share it with other people.

Story Board (2017)
Remember:
- There is no turning back once you press send.
- Even if you use apps like Snapchat the person can take a screen shot
- You risk being seen as someone you are not.
- Inappropriate content
Internet users must be careful of the sites they visit, as there are many sites with sex, violence, racial comments and other unlawful activities. Some of these sites can be entered even when parental control is switched on.
According to Roberts Blog (2016), inappropriate conduct has an intense effect on society as it is easier for people to behave inappropriately over the internet where they can remain anonymous. Inappropriate conduct can also negatively affect society as almost anyone in the world can be reached via the internet which can lead to all the negative impacts as described above.
A short summary of Virginia Shea’s “Netiquette” rules, can guide users of the internet to behave in a proper and acceptable manner (Deva, 2016 & http://www.albion.com/bookNetiquette/0963702513p32.html ). The rules are:
- Rule 1. Remember the human. Treat others in the same way you would like to be treated. Do not hurt other people’s feelings.
- Rule 2. Adhere to the same standards of behaviour online that you follow in real life – be ethical.
- Rule 3. Know where you are in cyberspace due to netiquette that varies from domain to domain.
- Rule 4. Respect other people’s time and bandwidth. Do not think that what you are busy doing is more important than what others are doing. Refrain from asking stupid questions and post messages to the correct discussion group. Conserve bandwidth when you retrieve information from a host or server.
- Rule 5. Make yourself look good online. Check grammar and spelling before you post and make sure you know what you are talking about. It must make sense.
- .Rule 6. Share expert knowledge. Offer your help to people of your discussion group if they ask questions
- Rule 7. Help keep flame wars under control. Refrain from posting spelling or grammar flames. Don’t respond to flame-bait. If you have started a flame war, apologise.
- Rule 8. Respect other people’s privacy. Don’t read other people’s private email.
- Rule 9. Don’t abuse your power. Use your power well.
- Rule 10. Be forgiving of other people’s mistakes. Remember that you were a network newbie once too.